While cybersecurity focuses on building strong walls to keep attackers out, cyber resilience acknowledges that breaches can still happen. It’s about adapting, responding, and recovering from cyberattacks with minimal disruption. So, why is cyber resilience becoming such a hot topic? Let’s dive deeper and explore why this shift in focus is critical for businesses in the digital age.
Cybersecurity vs. Cyber Resilience
Let’s unpack the difference between these two crucial concepts.
Cybersecurity is crucial for digital protection. It involves fortifying systems and data against cyberattacks. Firewalls block unauthorized access, antivirus software protects from malware, and strong passwords deter intruders. Cybersecurity creates a shield around your digital realm, preventing infiltration.
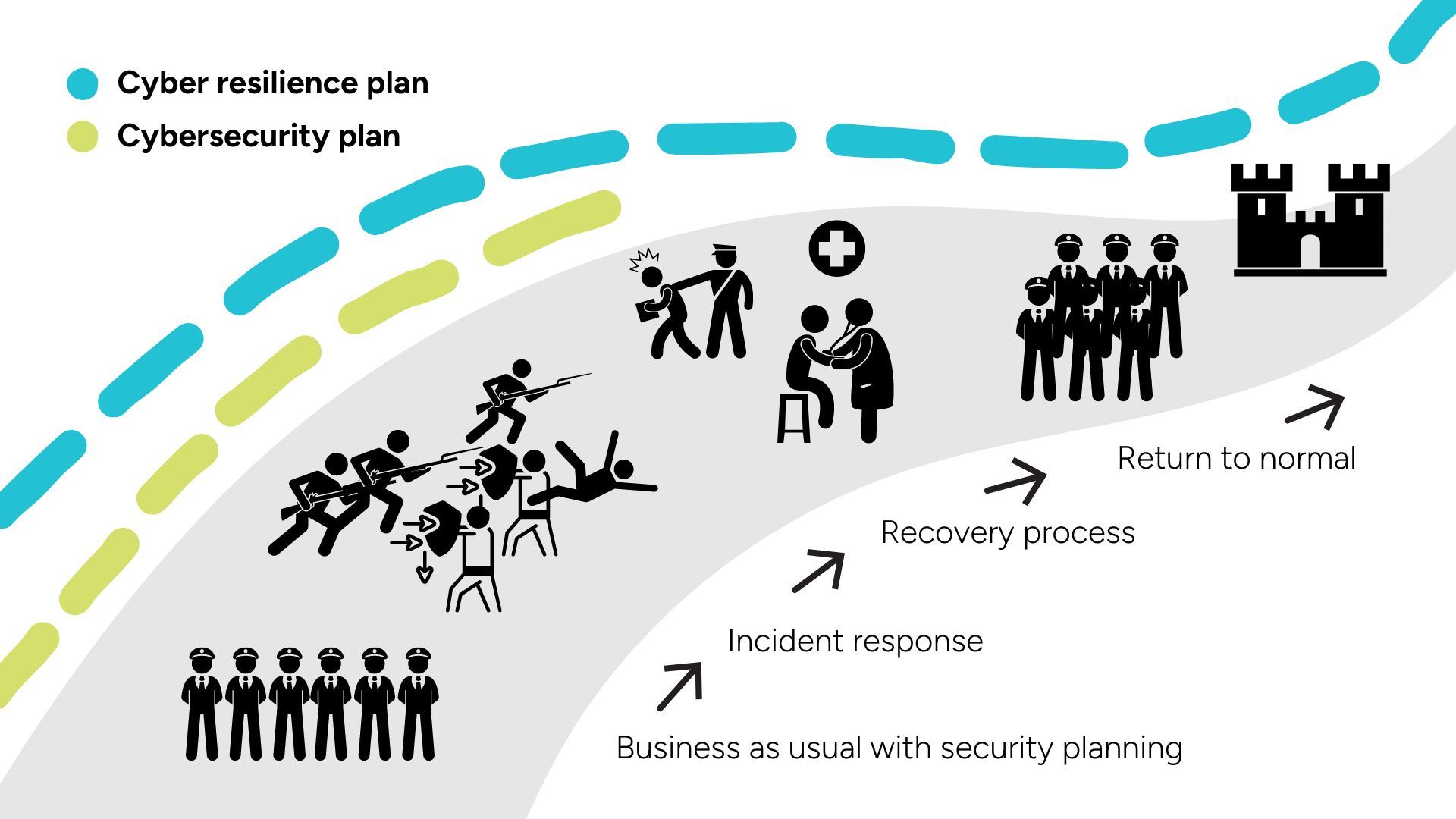
Cyber resilience, on the other hand, takes a more comprehensive view. It recognizes that breaches may occur despite preventive measures. Resilience enables organizations to recover swiftly from an attack, minimize harm, and quickly resume normal operations. Cyber resilience incorporates all cybersecurity tools, yet it extends beyond them, providing an encompassing strategy to withstand and bounce back from digital threats. It includes:
- Incident response plans: These outlines define clear steps to take when a breach occurs, minimizing confusion and ensuring a swift response.
- Business continuity (BC) plans: These plans ensure critical business functions can continue even during a disruption caused by a cyberattack.
- Disaster recovery (DR) plans: These plans focus on restoring essential IT infrastructure and data after a cyberattack.
While cybersecurity focuses on prevention, cyber resilience is all about preparation, response, and recovery. It’s the ability to weather the storm and emerge stronger on the other side.
Why prioritize cyber resilience
While cybersecurity remains a vital first line of defense, here’s why prioritizing cyber resilience offers a more comprehensive approach for businesses:
- Breaches are inevitable: No security system is perfect. Cybercriminals are constantly evolving their tactics, and even the most robust defenses can be breached.
- Focus on recovery, not just prevention: Cyber resilience acknowledges the possibility of a breach and focuses on minimizing its impact. By having a recovery plan in place, businesses can bounce back faster and minimize downtime.
- Reduced financial losses: Ransomware attacks and data breaches can be incredibly expensive. A cyber resilience plan can help businesses avoid paying ransoms and limit the financial fallout from a successful attack.
- Maintaining business continuity: Cyberattacks can disrupt critical operations. A cyber resilience plan ensures businesses have procedures in place to maintain essential functions even during an attack.
- Improved customer confidence: Data breaches can erode customer trust. By demonstrating a commitment to cyber resilience, businesses can show customers they take data security seriously.
- Enhanced brand reputation: A swift and effective response to a cyberattack can minimize reputational damage and even strengthen a brand’s image.
- Reduced legal risk: Regulations around data protection are becoming increasingly stringent. A cyber resilience plan can help businesses comply with these regulations and mitigate the legal risks associated with data breaches.
- Proactive approach to security: Cyber resilience goes beyond reactive measures. It encourages a proactive approach to security by identifying and addressing potential vulnerabilities before an attack occurs.
By prioritizing cyber resilience, businesses can move beyond simply preventing breaches and build a comprehensive security strategy that ensures preparedness, response, and recovery.
Case Study: Colonial Pipeline Ransomware Attack and Cyber Resilience
In May 2021, the Colonial Pipeline, a critical piece of US infrastructure responsible for transporting nearly half of the East Coast’s fuel supply, fell victim to a ransomware attack by the DarkSide group. Hackers gained access to the company’s systems, stole data, and encrypted essential files, forcing a shutdown of the pipeline. This caused fuel shortages, panic buying, and price hikes.
While the specifics of Colonial Pipeline’s cyber resilience plan are not publicly available, let’s explore how a robust plan could have minimized the impact of the attack:
- Strong backups: A key element of cyber resilience is having secure and readily accessible backups of critical data. If Colonial Pipeline had maintained up-to-date backups, they could have potentially restored their systems without paying the ransom or relying on potentially unreliable decryption tools offered by attackers.
- Faster recovery: A well-defined incident response plan would have outlined clear steps for containment, eradication, and recovery. This could have minimized downtime and expedited the restoration process, reducing the disruption to fuel supplies.
- Reduced financial impact: The decision to pay the ransom was likely influenced by the potential economic losses if the shutdown continued. A cyber resilience plan could have helped Colonial Pipeline weather the storm without resorting to paying the attackers, saving them millions of dollars.
The takeaway
The Colonial Pipeline attack serves as a reminder of the importance of cyber resilience. While prevention is crucial, a well-defined cyber resilience plan can significantly reduce the impact of a successful attack. By having secure backups, a clear incident response plan, and a focus on business continuity, companies can minimize downtime, financial losses, and reputational damage in the wake of a cyberattack.
Source: CISA (Cybersecurity & Infrastructure Security Agency), Deloitte US
Building a cyber resilient organization
To truly be prepared for any data threats, businesses need to build a comprehensive cyber resilience program. This goes beyond prevention and focuses on an organization’s ability to adapt, respond, and recover from cyberattacks with minimal disruption. The key lies in integrating cybersecurity efforts seamlessly with other critical functions.
Instead of viewing cybersecurity as a siloed entity, a holistic approach is necessary. This means tightly weaving cybersecurity practices into your incident response, business continuity, and disaster recovery plans. By creating a unified security strategy, you ensure a coordinated and efficient response to any cyber threat, minimizing damage and downtime.
Key aspects of a cyber resilience program:
- Incident response plan: This plan outlines clear steps for detecting, containing, and eradicating a cyberattack. It defines roles, responsibilities, and communication protocols to ensure a swift and coordinated response.
- Business continuity (BC) plan: A BC plan focuses on maintaining critical business functions during and after a disruption. This may involve implementing alternative solutions, activating backup systems, or prioritizing essential tasks.
- Disaster recovery (DR) plan: While similar to a BC plan, DR focuses specifically on restoring essential IT infrastructure and data after a cyberattack. This includes procedures for data recovery, system restoration, and testing of backups.
- Employee training and awareness: Human error is a significant factor in cyberattacks. Regularly training employees on cybersecurity best practices, phishing scams, and social engineering tactics can significantly reduce risk.
- Regular security assessments and exercises: Conducting regular vulnerability assessments and penetration testing proactively identifies weaknesses in your defenses. Additionally, simulating cyberattacks through exercises helps refine response plans and train employees.
- Defining “normal business operations”: Knowing what your “normal” operations look like helps determine the scope of disruption caused by a cyberattack. This is critical for establishing realistic recovery timelines and ensuring a complete return to functionality.
By implementing these key aspects, you can build a robust cyber resilience program that prepares your organization for any cyber threat.
Conclusion
In today’s digital battlefield, strong cybersecurity is essential, but it’s not enough. Cyber resilience takes your defenses a step further. It acknowledges that breaches can happen and focuses on your organization’s ability to adapt, respond, and recover quickly.
Think of it like this: cybersecurity is your shield, deflecting attacks. Cyber resilience is your emergency plan, ensuring you bounce back quickly.
Both are crucial. By prioritizing cyber resilience, businesses build a comprehensive security strategy for preparedness, response, and recovery. They can weather cyberattacks, minimize damage, and ensure business continuity.
Don’t leave your business vulnerable. STORViX offers a comprehensive suite of solutions that can help you build both a strong cybersecurity posture and a robust cyber resilience plan. We offer secure data storage solutions as the foundation, along with the tools and expertise to develop a complete incident response strategy and ensure business continuity.
Contact us to learn more about how we can help you build a cyber resilient future for your business.


